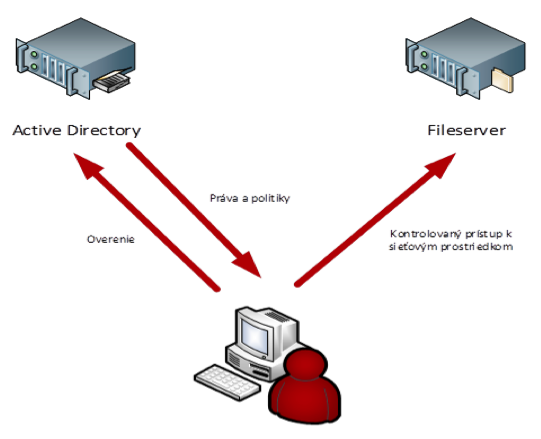
Active Directory (AD) is a database and set of services that connect users to the network resources they need to do their jobs.
The database (or directory) contains important information about your environment, including which users and computers are there and who has what to do what. For example, a database might contain 100 user accounts with details such as each person's job title, phone number, and password.
Services manage much of the activity that takes place in your IT environment. In particular, they make sure that each person is who they say they are (authentication), usually by checking the user ID and password they enter and only allowing them access to the data they can use (authorization).
The main Active Directory service is Active Directory Domain Services (AD DS), which is part of the Windows Server operating system. The servers that run AD DS are called domain controllers (DCs). Organizations typically have multiple DCs, and each DC has a copy of the directory for the entire domain. Changes made to the directory on one domain controller-such as updating a password or deleting a user account-are replicated to the other DCs so that they all remain up to date.
A global catalog server is a DC that stores a full copy of all objects in its domain directory and a partial copy of all objects of all other domains in the forest; this allows users and applications to find objects in any domain. Desktops, laptops, and other Windows devices (instead of Windows Server) can be part of an Active Directory environment, but they do not run AD DS. AD DS relies on several established protocols and standards it is important to understand that Active Directory is only for on-premises Microsoft environments.
Microsoft environments in the cloud use Azure Active Directory, which serves the same purposes as its namesake. AD and Azure AD are separate, but can work together to some extent if your organization has both on-premises and cloud IT environments (hybrid deployments).
The Active Directory database (directory) contains information about AD objects in the domain. Common types of AD objects include users, computers, applications, printers, and shared folders. Some objects may contain other objects (which is why you will see AD described as "hierarchical"). Organizations often simplify management by organizing AD objects into organizational units (OUs) and streamline security by placing users into groups. These OUs and groups are themselves objects stored in a directory.
Objects have attributes. Some attributes are obvious and some are more behind the scenes. For example, a user object usually has attributes such as a person's name, password, department, and email address, but also attributes that most people will never see, such as a globally unique identifier (GUID), a security identifier (SID), the last login time, and group membership.
Databases are structured, which means that there is a design that specifies what types of data they store and how that data is organized. This design is called a schema. Active Directory is no exception: Its schema contains formal definitions for each object class that can be created in the Active Directory domain structure and each attribute that can exist in an Active Directory object.,
The AD domain allows centralized management of user accounts, groups, workstations, domain policies, email accounts, etc. In this variant, permissions are handled on the basis of access groups to individual fileserver directories; users inherit settings based on their group assignments, regardless of which computer in the domain they log on to.
Therefore, adding systems and users to a domain is in most cases simply a matter of adding them to appropriate groups or copying an existing profile. The benefits of using Active Directory are many, for example central authentication, the ability to extend the AD schema to support mailboxes/instant messaging, integration with most MS-based systems, the ability to use group-specific policies, and more.
User accounts should be unique, the user must be specifically defined by a username and authenticated by a password. The system must allow setting different rights and permissions for individual users and their easy management, while preventing unauthorised access to data. The password shall be applied to all resources on the network.
How to choose the right IT Outsourcing? There are many companies on the market that offer the same range of services at similar prices.
Who should you entrust with the security of your systems? How to get security?
The first step to your satisfaction is to map your current technologies. Our experts will explain to you on the basis of a free IT audit,
what state your IT is in. We'll show you potential problems and present you with solutions. You have the opportunity to get to know us personally and make a no-obligation decision,
whether you want to work with us. Who are our long-term customers and why did they choose us? Read on.




Copyright © 2026 Všetky práva vyhradené